New in version 1.5: Enterprise
Differentiating the role level in WAPT¶
Hint
Feature only available with WAPT Enterprise
Introduction¶
WAPT offers the possibility to differentiate administrator roles based on a PKI to sign packages and actions.
Hint
The following description of roles differentiation is temporary as it will evolve in the near future.
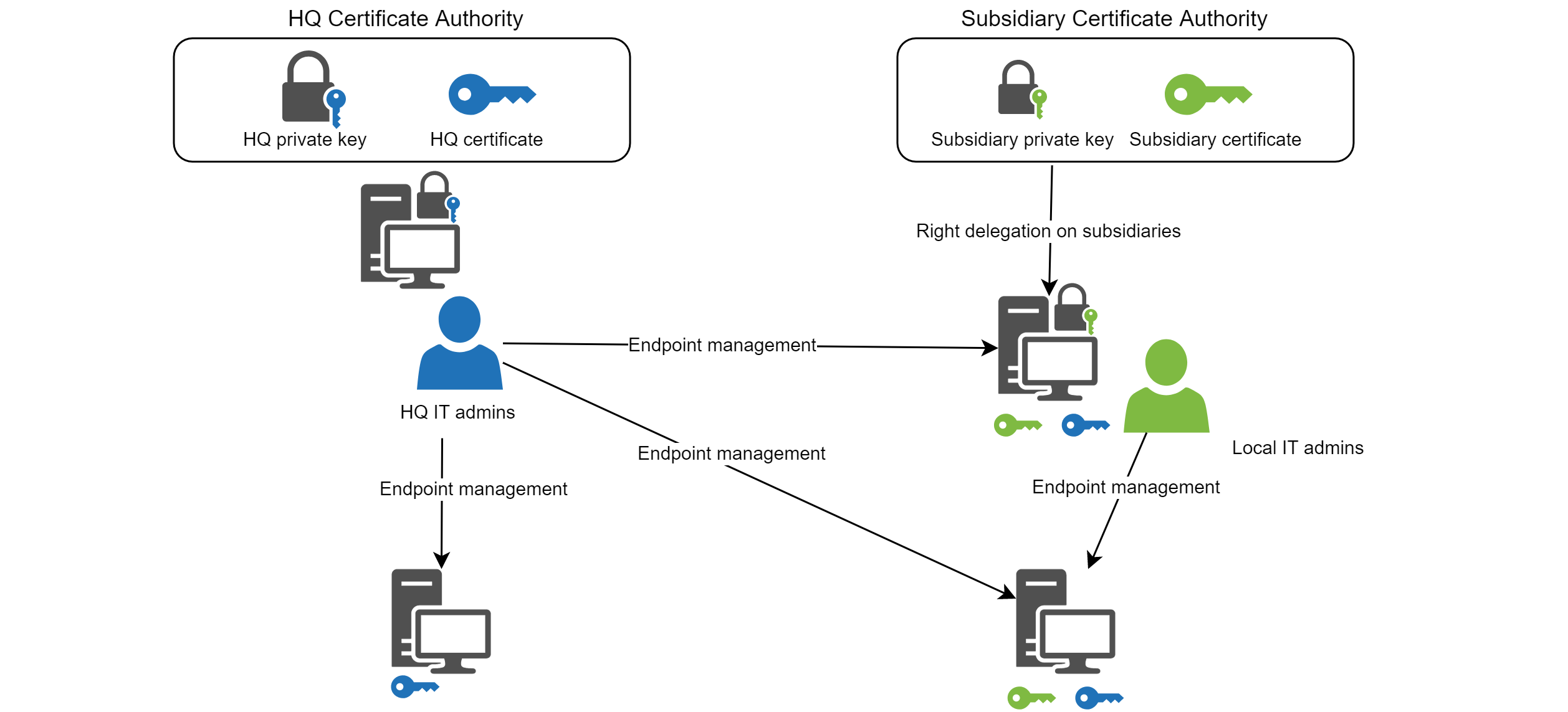
WAPT admin users roles differentiation¶
There are three cases:
Private key + certificate types |
Key usages |
|---|---|
Simple private key + certificate |
Allows authentication on WAPT console + interactions with WAPT agents |
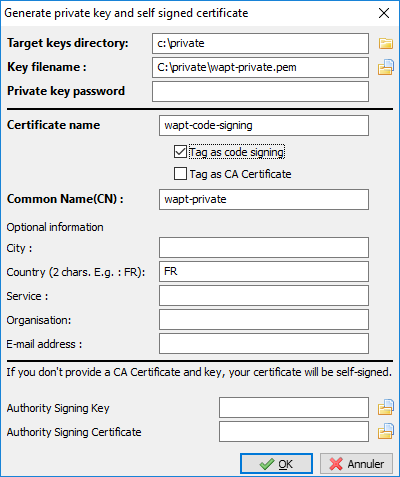
Developer private key + certificate |
Allows authentication on WAPT console + interactions with WAPT agents + package signing |
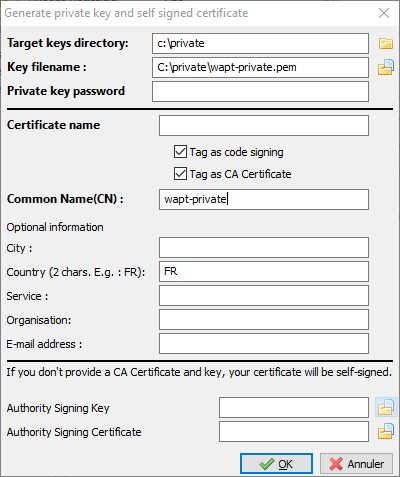
Certificate Authority (CA) private key + certificate |
Allows authentication + interactions + package signing + private key issuing |
Common WAPT install will generate a CA private key by default, allowing private key issuing for developers and package signing.
It is possible to emit a Certificate Authority for each subsidiaries. It is then possible to issue a personal private key and its corresponding certificate to each IT admins.
By looking at the above schematics, we can deduce the following conclusion:
WAPT agents in HQ can be managed by HQ IT team and cannot be managed by subsidiaries IT teams;
WAPT agents in the subsidiary having both certificates, from HQ and subsidiary, can be managed by local IT team and by HQ IT team;
The usage of an existing PKI is possible, WAPT Console comes with a simple certificate generator.
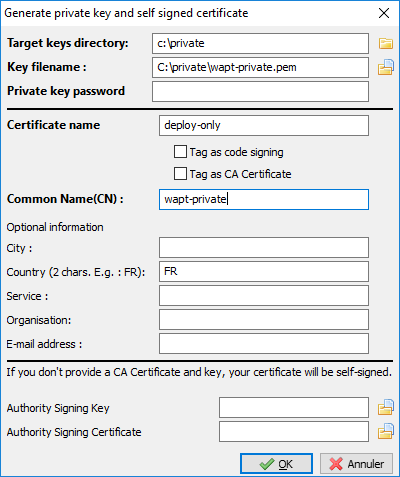
Generating a new certificate¶
Generating a new self-signed certificate¶
Deploying certificates of local IT admins on client¶
Some Organisations will choose to let local IT administrators perform actions on WAPT equipped devices by issuing them personnal certificates that will work on the set of devices for which the local IT admins are responsible.
The headquarter IT admins will deploy the certificates of local IT admins on the computers that local admins manage on their respective sites.
This way, local IT admins will not be able to manage computers located in headquarters, but on their own sites only.
You will need to copy the certificates of allowed local IT admins
on client in C:\program files(x86)\wapt\ssl.
Hint
Do not forget to restart the WAPT service on clients for them to use their new certificate. Open a command line cmd.exe then:
net stop waptservice
net start waptservice
If you want to deploy the certificates using WAPT, below is an example of a package to deploy certificates on client computers.
# -*- coding: utf-8 -*-
from setuphelpers import *
uninstallkey = []
def install():
print(ur"Copy of AC's distant site")
filecopyto('ca_distant.crt',makepath(install_location('WAPT_is1'),'ssl',))
def audit():
print('Auditing %s' % control.asrequirement())
return "OK"
if __name__ == '__main__':
update_package()