Generating the Administrator’s certificate for signing WAPT packages¶
Introduction¶
Naming conventions¶
name of the private key:
wapt-private.pem;public certificate signed with private key:
wapt-private.crt;
Private key wapt-private.pem¶
Attention
The wapt-private.pem file is fundamental for security.
It must be stored in a safe place and correctly protected.
The wapt-private.pem file is the private key, it is located by default
in the C:\private folder of the Administrator workstation.
For better security this private key may be transfered on an external storage. A smartcard support is in the roadmap.
This private key will be used along with the certificate to sign packages before uploading them onto the WAPT repository.
public certificate signed with private key: wapt-private.crt¶
The wapt-private.crt file is the public certificate that is used
along with the private key. It is by default created in the C:\private
folder, copied in C:\Program Files (x86)\wapt\ssl of the Administrator
and deployed on the desktops managed by the Administrator
via a WAPT package or a GPO.
This certificate is used to validate the signature of packages before installation.
Creating a certificate¶
In the WAPT console go to ;
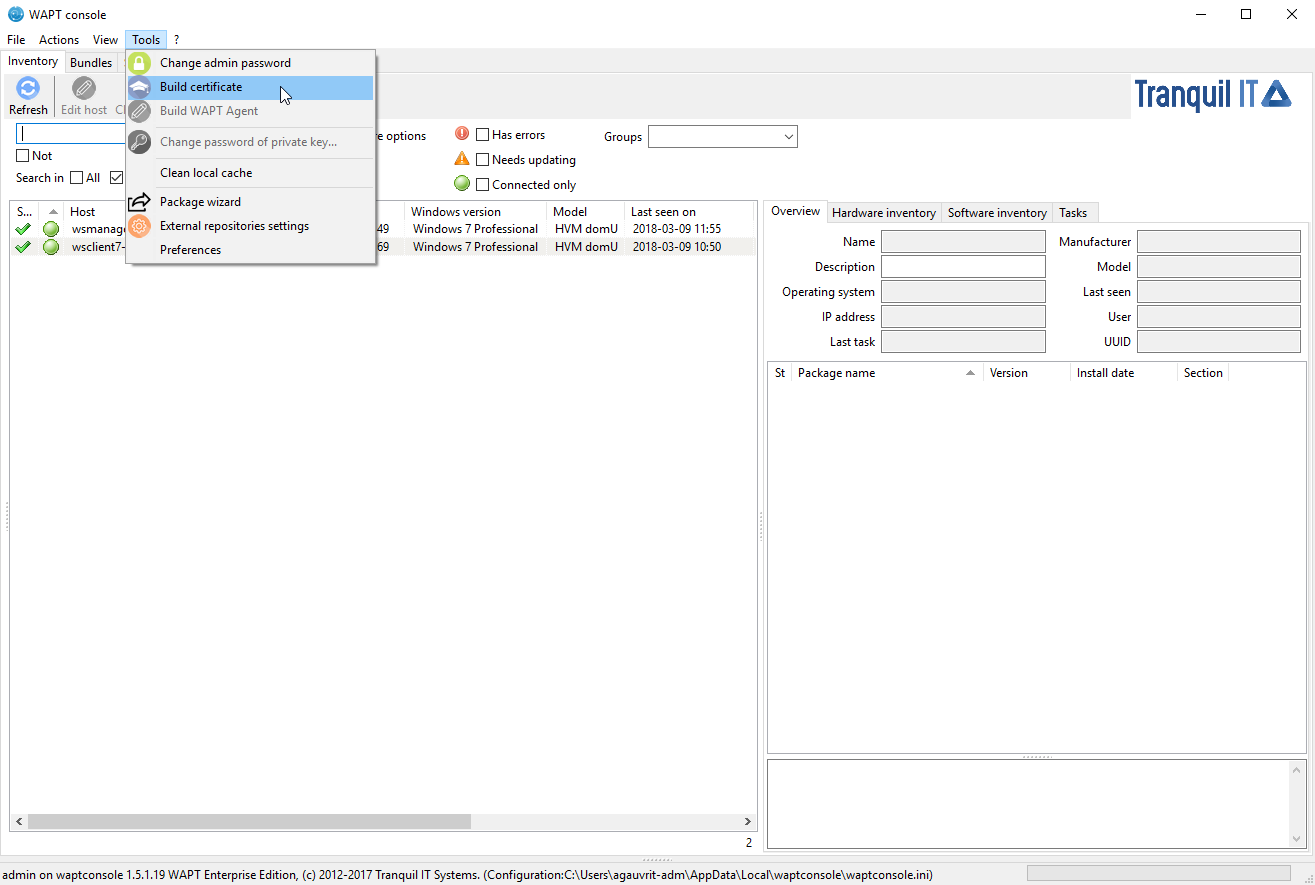
Creating a self-signed certificate¶
Important
We have two different options:
Creating a certificate - WAPT Community¶
fill in the following fields:
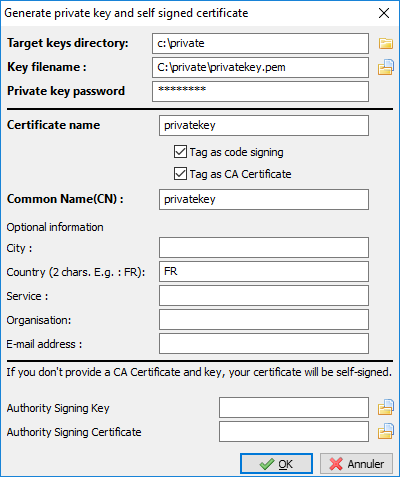
Creating a self-signed certificate¶
click on OK to go on to the next step;
Required informations are:
Destination folder: folder where the private key and the public certificate will be stored: required;
Name of the private key: name of the
.pemand Name of the private key;Private key password: password for locking and unlocking the key: required;
Private key password: password for locking and unlocking the key: required;
Common Name (CN): name of the Administrator: required;
Certificate name: name of the
.crtcertificate: required;Additional information: additional details stored in the private key. This information will help with identifying the origin of the WAPT package: optional;
For a fresh install, you can follow the screenshot below.
Hint
The password complexity must comply with your Organization’s security requirements (eg. ANSSI password recommendations).
Danger
the path to your private key must not be in the installation path of WAPT (
C:\Program Files (x86)\wapt);if your key is stored in
C:\Program Files (x86)\wapt, your Administrator private key will be deployed on your clients, absolutely a no go!
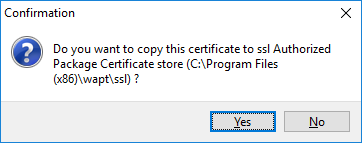
Confirmation of the copy of the certificate in the ssl folder¶
click on Yes to copy the newly generated certificate in the
C:\Program Files (x86)\wapt\sslfolder. This certificate will be picked up during the compilation of the WAPT agent and deployed on the client computers;
If everything has gone well the following message will appear:
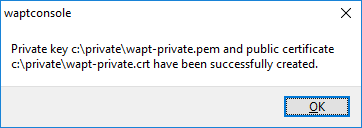
Certificate generated successfully¶
click on OK to go on to the next step;
You may go on to the next step and configure your WAPT console!!
Creating a certificate - WAPT Enterprise¶
With WAPT Enterprise, you can create a Master key with a Certificate Authority flag that can both sign packages and sign new certificates.
Hint
In order to create new signed certificates for delegated, please refer to Differentiating the role level in WAPT.

Creating a self-signed certificate¶
Required informations are:
Destination folder: folder where the private key and the public certificate will be stored: required;
Name of the private key: name of the
.pemand Name of the private key: name of the.pemand.crtfiles: required;Private key password: password for locking and unlocking the key: required;
Common Name (CN): name of the Administrator: required;
Certificate name: name of the
.crtcertificate: required;Code signing: check this box if the certificate/ key pair will be allowed to sign software packages: required;
CA certificate: check this box if this certificate can be used to sign other certificates (main or intermediate Certificate Authority): required;
Additional information: additional details stored in the private key. This information will help with identifying the origin of the WAPT package: optional;
Hint
The password complexity must comply with your Organization’s security requirements (eg. ANSSI password recommendations).
Note
If your Organization is already equipped with an Certificate Authority (CA), you will have to fill the certificate and the key in the fields CA Certificate and CA Key.
With this procedure you can generate new certificates/ key pairs with or without Code Signing capability.
Danger
the path to your private key must not be in the installation path of WAPT (
C:\Program Files (x86)\wapt);if your key is stored in
C:\Program Files (x86)\wapt, your Administrator private key will be deployed on your clients, absolutely a no go!

Confirmation of the copy of the certificate in the ssl folder¶
click on Yes to copy the newly generated certificate in the
C:\Program Files (x86)\wapt\sslfolder. This certificate will be picked up during the compilation of the WAPT agent and deployed on the clients computers;
If everything has gone well the following message will appear:

Certificate generated successfully¶
click on OK to go on to the next step;
You may go on to the next step and configure your WAPT console.