Using the WAPT console advanced¶
This page details the advanced use of the WAPT console.
Using profile bundles in WAPT  ¶
¶
Working principle¶
WAPT Enterprise offers Active Directory profile bundle functionality.
It automates installation of WAPT software and configuration packages on hosts, based on their membership to Active Directory Computer Security Groups.
Important
Active Directory Computer’s security groups contains Computers, not Users.
Warning
Automatically installing software and configurations based on user and user group membership is not implemented with WAPT and such implementation is not desirable. The use case of installing oftware based on user profile is better served with the differentiated self-service feature that is also available with WAPT Enterprise.
Creating profile bundle packages in WAPT console¶
You can create profile bundle packages by clicking on .
Important
Requirements:
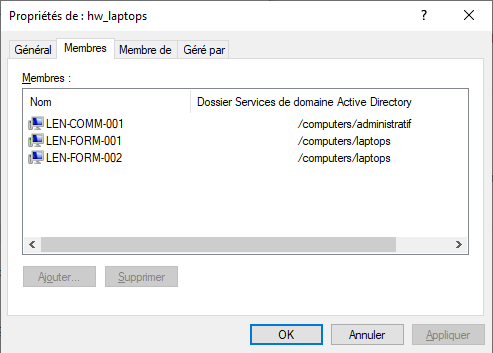
The profile package name must be exactly the same as the AD Security group name.
The profile package name is case sensitive.
Example:
AD Security group:
HW_laptops;WAPT profile bundle:
HW_laptops;
A window opens and you are prompted to choose which packages must be in the just created profile bundle.
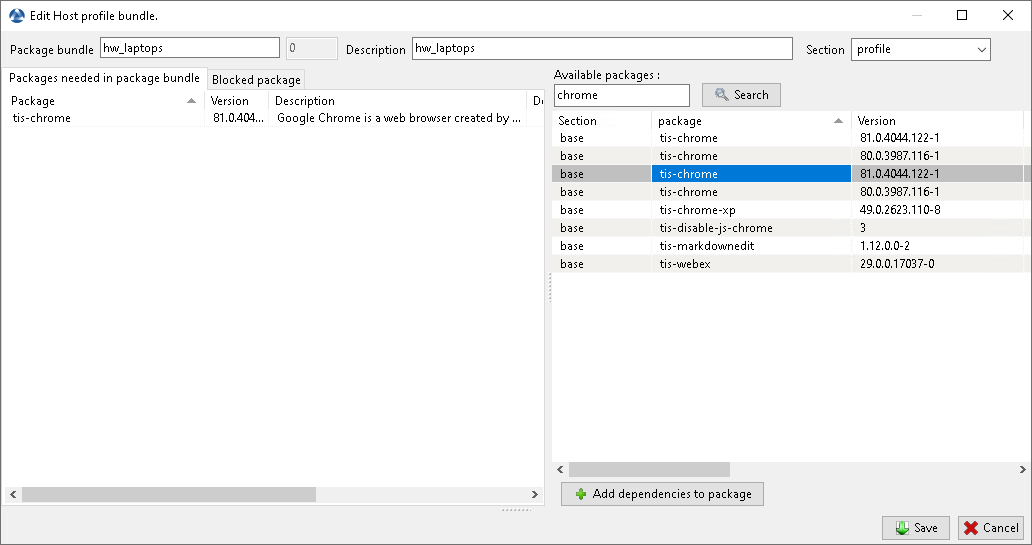
Adding package to profile bundle¶
Save the profile bundle package and it will be uploaded to the WAPT server.
Using Organizational Unit packages in WAPT  ¶
¶
Working principle¶
WAPT Enterprise offers Organizational Unit packages functionality.
It automates software installations based on your Active Directory organization.
The WAPT agent is aware of its position in the Active Directory tree structure, therefore it knows the hierarchy of Organizational Units that concerns it, for example:
DC=ad,DC=domain,DC=lan
OU=Paris,DC=ad,DC=domain,DC=lan
OU=computers,OU=Paris,DC=ad,DC=domain,DC=lan
OU=service1,OU=computers,OU=Paris,DC=ad,DC=domain,DC=lan
If an Organizational Unit package is defined on each level, the WAPT agent will automatically download packages and configurations that are attached to each level. Using inheritance, WAPT will apply packages and dependencies that have been attached to that Organizational Unit.
Creating Organizational Unit packages¶
You can create unit packages by .
A window opens and you are prompted to choose which packages must be included in the unit bundle.
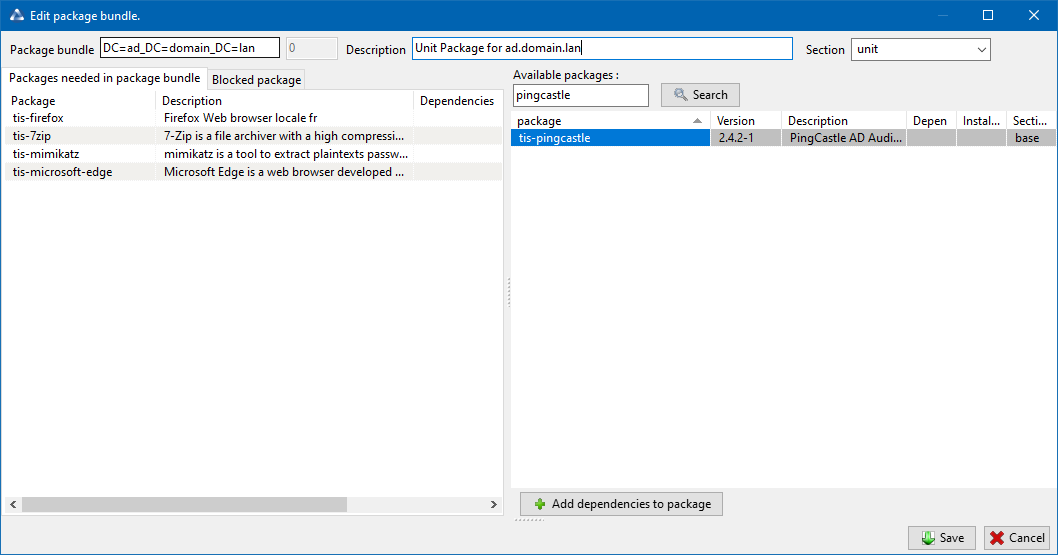
Adding package to unit bundle.¶
Save the package and it will be deployed to all hosts belonging to that OU.
Actions available with Organizational Units¶
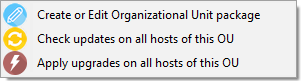
WAPT console showing options applicable to OU¶
You can see in the picture that update and upgrade actions can be performed through this menu, thus selecting hosts by their Organizational Unit.
Creating or Editing Organizational Unit package¶

Creating or editing OU packages¶
Visit this documentation for more details on Creating or editing OU packages.
Checking updates on all hosts of this OU¶
Checking updates for hosts in the OU¶
This button will execute 2 actions on all hosts in the OU:
Give current state of the host to the server.
Server displays if the host must get updates.
Applying upgrades on all hosts of the OU¶
Applying upgrades to hosts in the OU¶
This button allows to apply waiting updates on the all hosts in the OU.
Hint
- You may filter how hosts are displayed based on the Active Directory
OU they belong to.

Including hosts in subfolders¶
The checkbox Include hosts in subfolders allows to display hosts in subfolders.
Faking Organizational Units for WORKGROUP hosts¶
It can happen that some specific hosts cannot be joined to an Active Directory domain.
With that specificity, such hosts do not show up in your Active Directory Organizational Units in your WAPT Console.
To make all hosts show up in the console under the right Organizational Unit, whether they are joined to an AD domain or not, WAPT allows you to specify a fake Organizational Unit WAPT agent configuration file.
The benefits of this trick are:
You can manage these hosts with WAPT as if they where joined to the AD.
- Out-of-domain and workgroup hosts are now showing up
in a familiar Active Directory tree view.
Unit packages are usable on these hosts.
To setup a fake Organizational Unit on hosts, create an empty WAPT package, then use the following code:
# -*- coding: utf-8 -*-
from setuphelpers import *
uninstallkey = []
def install():
print('Setting Fake Organizational Unit')
fake_ou = "OU=TOTO,OU=TEST,DC=DEMO,DC=LAN"
inifile_writestring(WAPT.config_filename,'global','host_organizational_unit_dn',fake_ou)
print('Reload WAPT configuration')
WAPT.reload_config_if_updated()
def update_package():
pass
The host_organizational_unit_dn will be like below in wapt-get.ini:
[global]
host_organizational_unit_dn=OU=TOTO,OU=TEST,DC=DEMO,DC=LAN
Note
- Stick to a specific case with your
host_organizational_unit_dn (don’t mix “dc”s and “DC”s, “ou”s and “OU”s…).
- Stick to a specific case with your
Follow the case used in the DN/
computer_ad_dnfields in the hosts grid.
Using WAPT Windows Update Agent (WAPTWUA)  ¶
¶
WAPT is able to manage Windows Updates on your endpoints and replace automatic Windows update or a WSUS Server.
Note
- The internals of WAPTWUA is based on the WUA API.
For more information: https://docs.microsoft.com/en-us/windows/win32/wua_sdk/using-the-windows-update-agent-api
Working principle¶
Each Patch Tuesday,
the WAPT server downloads an updated wsusscn2.cab
file from Microsoft servers.
By default, downloads happen once a day and no download is triggered
if the wsusscn2.cab file has not changed since the last download.
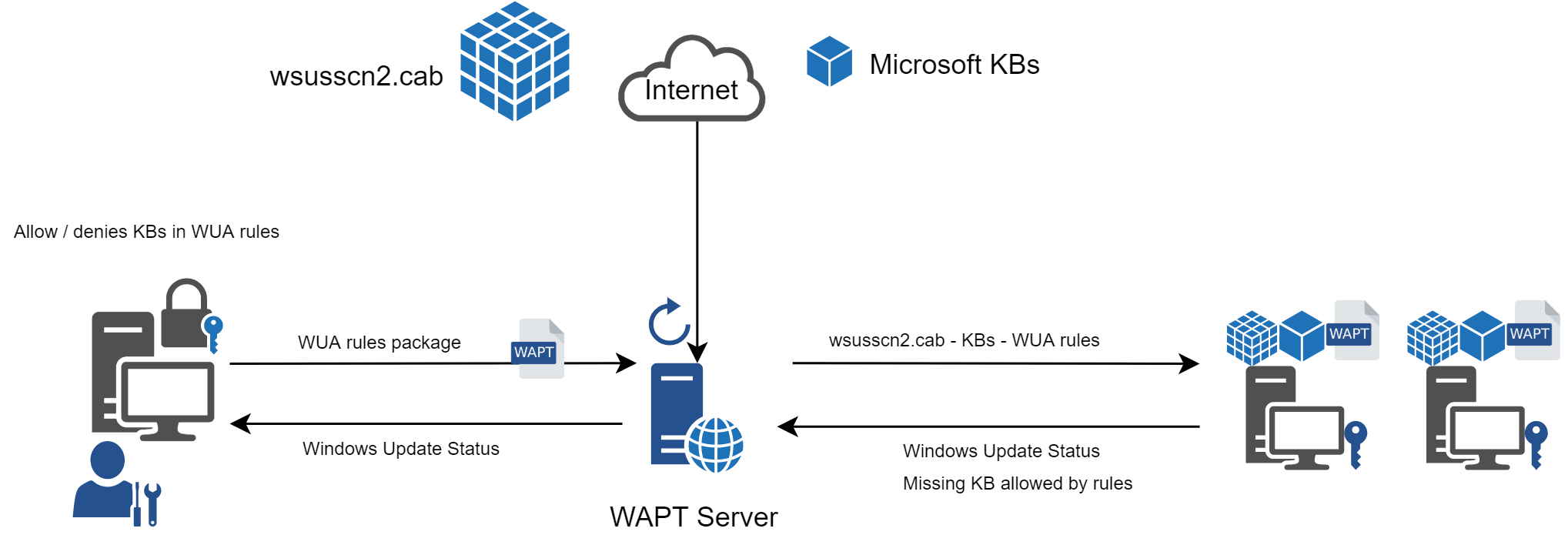
The wsusscn2.cab file is then downloaded by the WAPT agent
from WAPT server repository and then passed on to WUA
Windows utility to crunch the update tree for the host.
Regularly, the host will analyze the available updates using
the wsusscn2.cab file. The host will send its list of needed updates
to the WAPT server.
If an update is pending on the host and if that update is not present on the WAPT server, the server will download the needed update from official Microsoft servers.
Hint
- This mode of operation allows WAPT to download only the necessary updates
on the computers, thus saving bandwidth, download time and disk space.
Note
On the WAPT server, downloaded updates are stored:
On Linux hosts in
/var/www/waptwua.On Windows hosts in
C:\wapt\waptserver\repository\waptwua.
The WAPT Windows Update Agent repository download URL is based on the repo_url
parameter in wapt-get.ini:
- In case of repository replication, it is fully operational
with WAPT Windows Update to reduce bandwidth use.
- Do not forget to synchronize the
waptwuafolder if you are replicating your packages with distant repositories.
- Do not forget to synchronize the
Note
If in your company, a proxy is needed to go out on the Internet, then be sure to set the proxy server in the waptserver.ini file.
Difference between WAPT Windows Updates and WSUS¶
WSUS downloads by default the updates for selected categories. This can lead to a very large update database and lots of storage.
WAPT Windows Update only downloads updates that have been requested by at least one client computer. This helps to keep the local database small (a few 10s of Gigabytes) and it can be easily cleaned up if you want to recover space.
Major OS upgrades¶
Major OS upgrades are upgrades from one OS version to another. That includes, for example, upgrades from Windows 7 to Windows 10, or from Windows 10 1803 to Windows 10 1903.
Major version upgrades are not handled in the same way as minor OS upgrades. Major upgrades are handled via the downloading of the new install ISO content (same content as for a fresh install) and running the setup.exe with the correct parameters. This process is the same for WSUS, SCCM and WAPT Windows Updates.
In the case of WAPT Windows Updates, you need to create a OS update package using a template package provided on https://store.wapt.fr.
Driver upgrades¶
Driver upgrades via WSUS are not recommended since it is hard
to properly handle side effects. In the case of WAPT Windows Updates,
DRIVERS ARE NOT DOWNLOADED since they are not referenced
in the wsusscn2.cab files provided by Microsoft.
It is recommended to push driver updates via a custom WAPT package. If the driver patch is packaged as a .msu, you may package it as a standard WAPT package.
Just select the .msu file and click in the WAPT console to launch the wizard for simplified package creation.
If the driver update is packaged as a .zip containing the .exe file, you can create a WAPT package containing the necessary files and setup.exe binary with the correct silent flag.
Out of band KB¶
Microsoft sometimes provides OOB updates
that are not contained in the wsusscn2.cab index.
Those updates are not included in the main update because
they may fix a very specific problem or may have drawbacks in some situations.
If you want to deploy an OOB KB update, you can download it from the Microsoft catalog https://www.catalog.update.microsoft.com/Home.aspx.
Just select the .msu file and click in the WAPT console to launch the wizard for simplified package creation.
To do so, you may follow this documentation on packaging .msu files for these Out-of-band updates.
Attention
You have to be careful that OOB updates may break your system, be sure to read the prerequisites on the Microsoft bulletin corresponding to the update and thoroughly test the update.
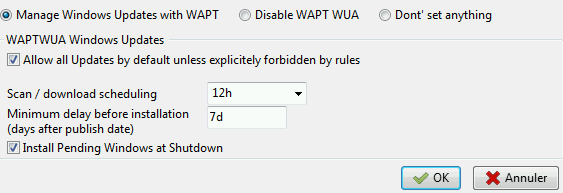
Configuring WAPTWUA on the WAPT agent¶
WAPTWUA is configured in wapt-get.ini in [waptwua] section.
You then have several options:
Options / Default Value |
Description |
Example |
|---|---|---|
|
Enable or disable WAPTWUA on this host. |
|
|
Download updates directly from Microsoft servers. |
|
|
Set if missing update is authorized or not by default. |
|
|
|
|
|
|
|
|
Install update when the machine will shutdown. |
|
|
Set a deferred installation delay before publication in the repository. |
|
|
|
|
Hint
These options can be set when generating the WAPT agent.
Example [waptwua] section in wapt-get.ini file:
[waptwua]
enabled =true
default_allow =False
direct_download=False
download_scheduling=7d
install_at_shutdown=True
install_scheduling=12h
install_delay=3d
When you create the waptagent.exe from your console,
these options are equivalent to this:
Example source code to modify [waptwua] settings by package:
def install():
inifile_writestring(WAPT.config_filename,'waptwua','enabled','true')
inifile_writestring(WAPT.config_filename,'waptwua','install_at_shutdown','true')
inifile_writestring(WAPT.config_filename,'waptwua','download_scheduling','7d')
inifile_writestring(WAPT.config_filename,'waptwua','allowed_severities','Critical,Important')
print('Reload WAPT configuration')
WAPT.reload_config_if_updated()
Using WAPTWUA from the console¶
The WAPTWUA are managed with two tabs in the WAPT console.
WUA Rules sub-tab in WAPT Package tab¶
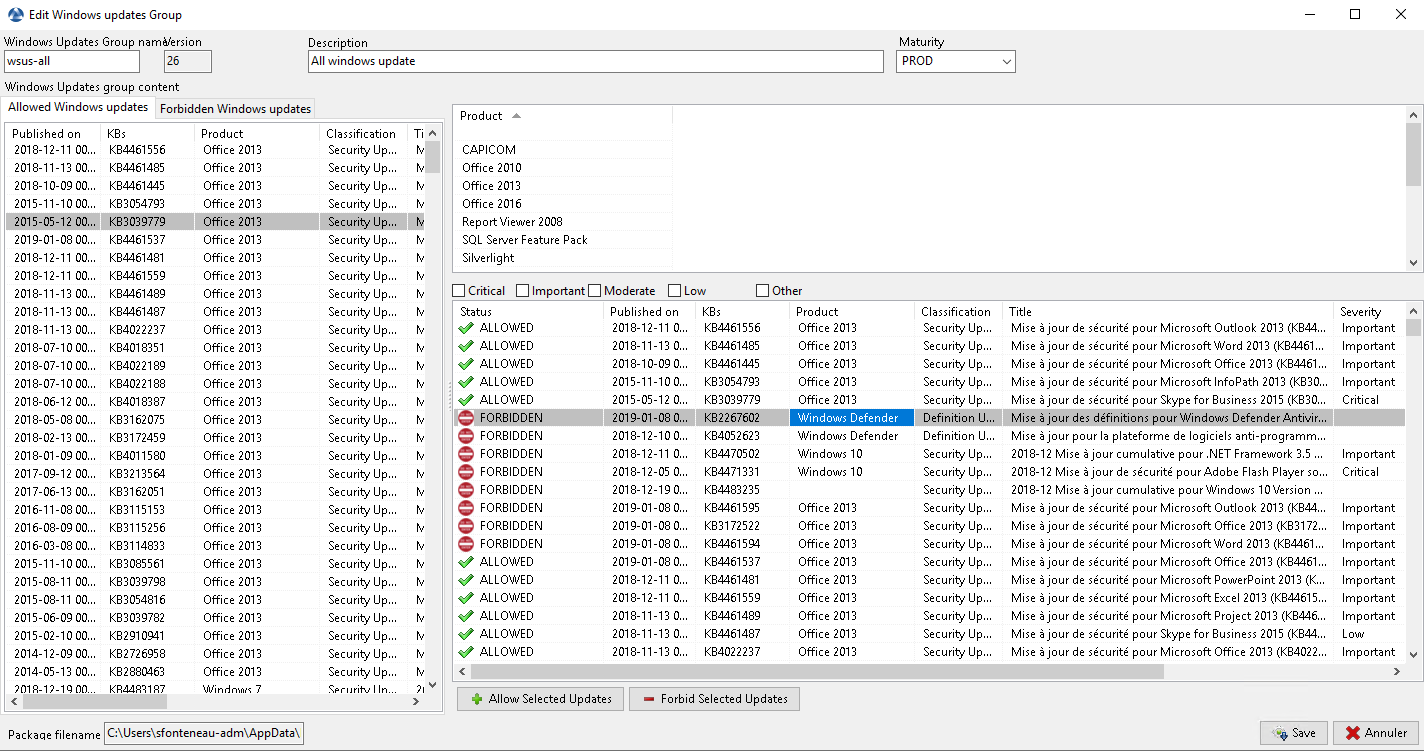
The WUA Rules tab allows you to create waptwua rules packages.
- When this type of package is installed on a machine,
it indicates to the WAPTWUA agent the authorized or forbidden KBs.
- When several waptwua packages are installed on a machine,
the different rules will be merged.
- When a
cabis neither mentioned as authorized, nor mentioned as prohibited, WAPT agents will then take the value of
default_allowinwapt-get.ini.
- When a
Note
If the WAPTWUA agent configuration is set to
default_allow = True, then it will be necessary to specify the forbiddencab.If the WAPTWUA agent configuration is set to
default_allow = False, then it will be necessary to specify the authorizedcab.
Hint
To test updates on a small set of computers, you can set WAPTWUA default maturity to
PREPROD.- You can then test the Windows Updates on a small sample of
PREPRODhosts and if everything is good, you can release the updates to the entire fleet of computers.
- You can then test the Windows Updates on a small sample of
Windows Updates tab¶
The Windows Update tab lists all needed Windows Updates.
Important
- The server does not scan the
wsussc2.cabitself, it lets the Windows Update Agent utility present on all Windows machines do it.
- If an update seems to you as missing from the list, you must run a scan
on one of the machines present in the console.
- If you run a WUA scan on a Windows 10 agent, the CAB and Windows 10 files
will be displayed on the Windows Update tab.
The left pane displays update categories, allowing you to filter by:
Criticality;
Product;
Classification;
In the right panel grid, if the Downloaded on column is empty, it means that the update has not yet been downloaded by the WAPT server and is not present on the WAPT server (This update is not missing on any host).
You can force the download of an update by .
You can also force the download of the
wsusscn2.cabfile with the Download WSUSScan cab from Microsoft Web Site button.You can see the Windows Updates download on the server with the Show download task button.
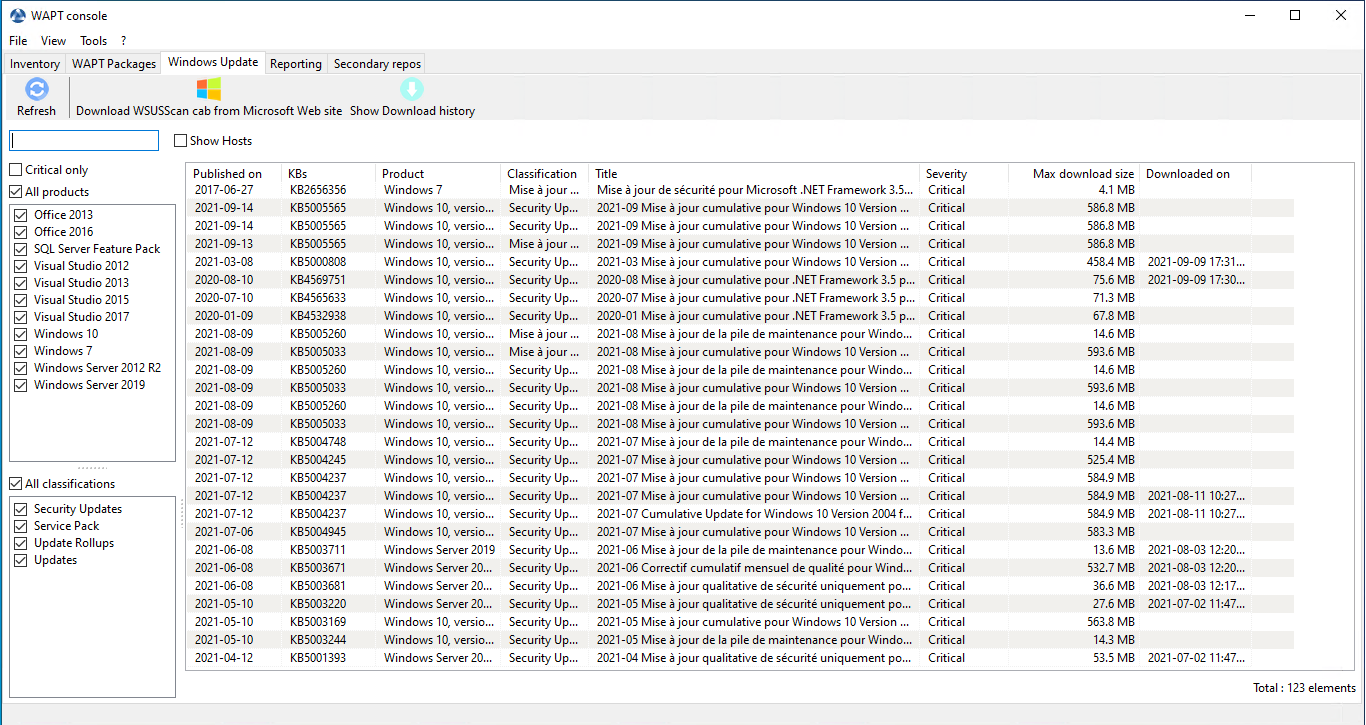
Listing of Windows Update¶
Hint
Every 30 minutes, the WAPT Server will look for updates that have been requested at least once by WAPT Clients and that have not yet been downloaded and cached. If an update is pending, the WAPT Server will download it from official Microsoft servers.
You can force this scan with the Download index and missing cabs from Microsoft Web site button in tab
Clean old Windows updates¶
To cleanup your waptwua folder, you can remove Windows Updates
that are no longer needed.
WAPT server will only re-download deleted updates if one of the WAPT equipped hosts requests it.
On the WAPT Server, downloaded updates are stored:
On Linux hosts in
/var/www/waptwua.On Windows hosts in
C:\wapt\waptserver\repository\waptwua.
Launching WUA on clients¶
From the console you have three options.
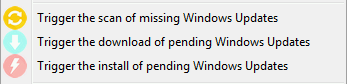
Windows Update action buttons available in the WAPT console¶
- The Trigger the scan of pending Windows Updates button
will launch the scan on the client and list all updates flagged for the OS.
- The Trigger the download of pending Windows Updates button
will launch the downloading of pending updates on the client.
- The Trigger the install of pending Windows Updates button
will launch the install of downloaded updates on the client.
Hint
When pending updates stored in cache need to be installed, the WAPT agent triggers the WUA service.
The WAPT agent will enable and start the WUA Service temporarily to install the updates. When updates are installed, waptservice will stop and disable the WUA service until the next cycle.
State of Update on host¶
Windows updates can have 4 states on a host.
Status |
Description |
|---|---|
OK |
A Windows update has installed correctly. |
MISSING |
A Windows update has not yet been downloaded to the WAPT server. |
PENDING |
|
DISCARDED |
A Windows update was forbidden by rules. |
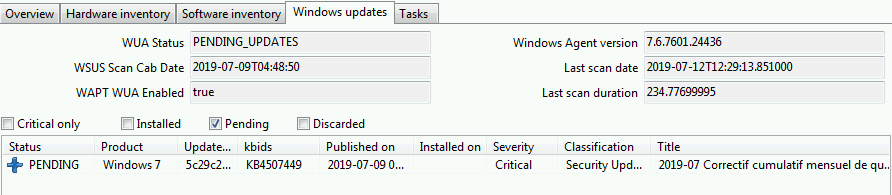
Pending Windows Updates showing in the WAPT console¶
Notion of UpdateID¶
In WAPT we don’t use kbids but instead we use updateids.
This allows us to be finer in the management of updates.
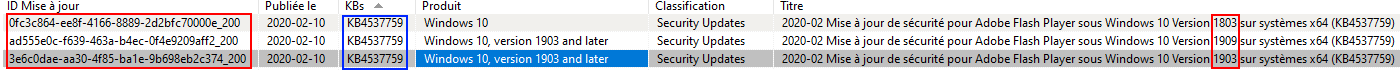
Duplicate kb¶
In this example, KB4537759 appears multiple times because there are 3 different updateids:
win10 1803;
win10 1903;
win10 1909;
You should therefore authorize updateids and not kb ids.
WAPT does not force Windows to uninstall a Windows Update¶
Uninstalling a Windows update can be dangerous for the machine. When an update is detected as forbidden by WAPT, its uninstallation will NOT be forced.
If you really want to uninstall an update, you should package the KB that you want to uninstall as a standard WAPT package.
Here is an example:
from setuphelpers import *
uninstallkey = []
def install():
with EnsureWUAServRunning():
run('wusa /uninstall /KB:4023057')
Video demonstration¶
Using the reporting functions in WAPT  ¶
¶
Working principle¶
WAPT Enterprise offers advanced reporting capabilities.
Indeed, who better than you to know what you want in your report.
With WAPT we offer to write your own SQL queries to display the result in the WAPT console, or to download already made queries from Internet.
WAPT query Designer¶
The query designer offers you the ability to edit your own queries on the WAPT PostgreSQL database.
To create a new report, click on .
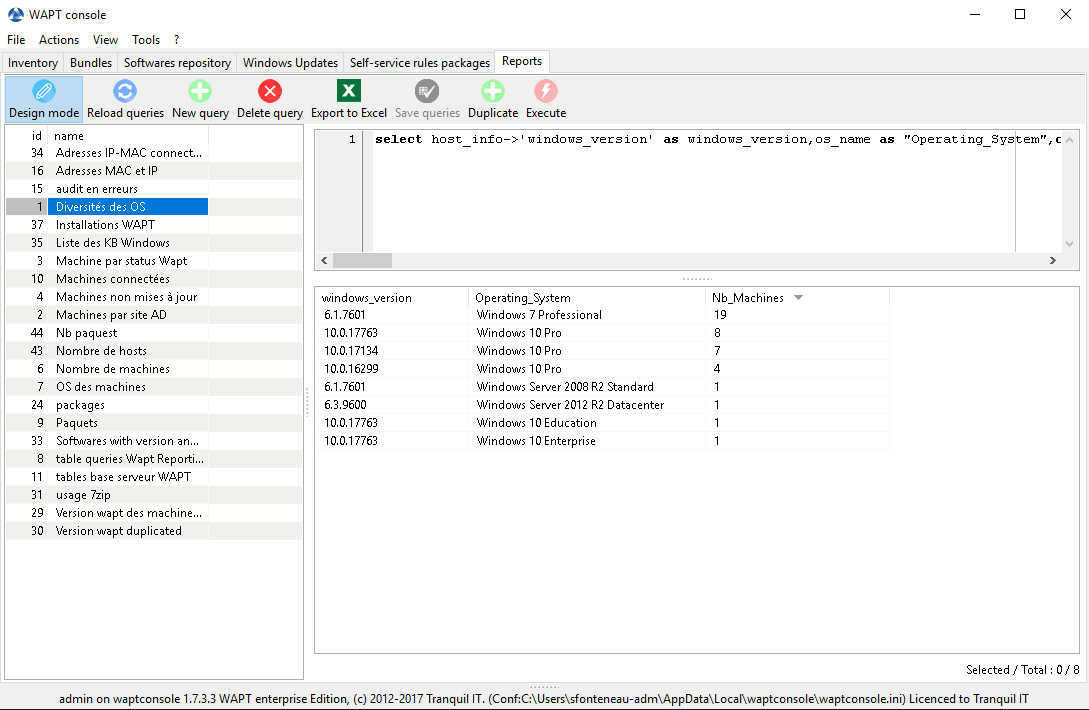
Designing a query in WAPT reporting¶
Hint
To rename a query, press the F2 key.
In the top banner, you can write your SQL query.
To edit / modify / save your reports:
The Reload queries button is used to reload queries saved on the server, for example, if a colleague has just edited a new query.
The New query button will add a new blank query to the list.
The Delete query button will delete the selected query from the WAPT Server.
The Export to Excel button will export the result of your query to a spreadsheet.
The Save queries button will save your query to the WAPT Server.
The Duplicate button will duplicate an existing query to avoid writing a request from scratch.
The Execute button executes the selected query.
Note
The queries are saved in the PostgreSQL WAPT database.
The shortcut CTRL+space allows you to build your queries more effectively as it will auto-complete some fields for you.
Query examples¶
Computers query¶
Counting hosts.
select count(*) as "Nb_Machines" from hosts
Listing computers.
select computer_name, os_name, os_version, os_architecture, serialnr from hosts order by 4,3,1
Listing computers MAC addresses and IP.
select distinct unnest(mac_addresses) as mac, unnest(h.connected_ips) as ipaddress, computer_fqdn,h.description, h.manufacturer||' '||h.productname as model, h.serialnr, h.computer_type from hosts h order by 1,2,3
Listing Windows versions.
select host_info->'windows_version' as windows_version, os_name as operating_system, count(os_name) as nb_hosts from hosts group by 1,2
Listing operating systems.
select host_info->'windows_version' as windows_version, os_name as "Operating_System", count(os_name) as "Nb_Machines" from hosts group by 1,2
Listing hosts not seen in a while.
select h.uuid, h.computer_fqdn, install_date::date, version, h.listening_timestamp::timestamp, h.connected_users from hostsoftwares s left join hosts h on h.uuid=s.host_id where s.key='WAPT_is1' and h.listening_timestamp<'20190115'
Filtering hosts by chassis types.
select case dmi->'Chassis_Information'->>'Type' when 'Portable' then '01-Laptop' when 'Notebook' then '01-Laptop' when 'Laptop' then '01-Laptop' when 'Desktop' then '02-Desktop' when 'Tower' then '02-Desktop' when 'Mini Tower' then '02-Desktop' else '99-'||(dmi->'Chassis_Information'->>'Type') end as type_chassis, string_agg(distinct coalesce(manufacturer,'?') ||' '|| coalesce(productname,''),', '), count(*) as "Nb_Machines" from hosts group by 1
Listing of hosts with their Windows Serial Key.
select computer_name, os_name, os_version, host_info->'windows_product_infos'->'product_key' as windows_product_key from hosts order by 3,1
WAPT query¶
Listing WAPT packages in WAPT server repository.
select package, version, architecture, description, section, package_uuid, count(*) from packages group by 1,2,3,4,5,6
Listing hosts needing upgrade.
select computer_fqdn, host_status, last_seen_on::date, h.wapt_status, string_agg(distinct lower(s.package),' ') from hosts h left join hostpackagesstatus s on s.host_id=h.uuid and s.install_status != 'OK' where (last_seen_on::date > (current_timestamp - interval '1 week')::date and host_status!='OK') group by 1,2,3,4
Packages query¶
Listing packages with their number of installation.
select package, version, architecture, description, section, package_uuid, count(*) from hostpackagesstatus s where section not in ('host','unit','group') group by 1,2,3,4,5,6
Software query¶
Listing WAPT Discovery agents.
select h.uuid, h.computer_name, install_date::date, version, h.listening_timestamp::timestamp, name from hostsoftwares s left join hosts h on h.uuid=s.host_id where s.key='WAPT_is1' and (name ilike 'WAPT%%Discovery%%' or name ilike 'WAPT %%')
Listing hosts with their 7zip version associated.
select hosts.computer_name, hostsoftwares.host_id, hostsoftwares.name, hostsoftwares.version from hosts, hostsoftwares where hostsoftwares.name ilike '7-zip%%' and hosts.uuid=hostsoftwares.host_id order by hosts.computer_name asc
Listing hosts with their software.
select n.normalized_name, s.version,string_agg(distinct lower(h.computer_name),' '), count(distinct h.uuid) from hostsoftwares s left join normalization n on (n.original_name = s.name) and (n.key = s.key) left join hosts h on h.uuid = s.host_id where (n.normalized_name is not null) and (n.normalized_name<>'') and not n.windows_update and not n.banned and (last_seen_on::date > (current_timestamp - interval '3 week')::date) group by 1,2
Listing normalized software.
select n.normalized_name, string_agg(distinct lower(h.computer_name),' '), count(distinct h.uuid) from hostsoftwares s left join normalization n on (n.original_name = s.name) and (n.key = s.key) left join hosts h on h.uuid = s.host_id where (n.normalized_name is not null) and (n.normalized_name<>'') and not n.windows_update and not n.banned and (last_seen_on::date > (current_timestamp - interval '3 week')::date) group by 1
You can also find several more examples of queries on Tranquil IT’s Forum.
Feel free to post your own queries on the same forum with an explanation of what your query does, ideally with a screen capture or a table showing a sample of your query result.
Normalizing software names¶
Sometimes, the version of the software or its architecture are an integral part of the software name. When they register with the WAPT Server inventory, they appear as different software whereas they are just one software for us humans.
To solve this problem, we propose to standardize the name of the software with WAPT.
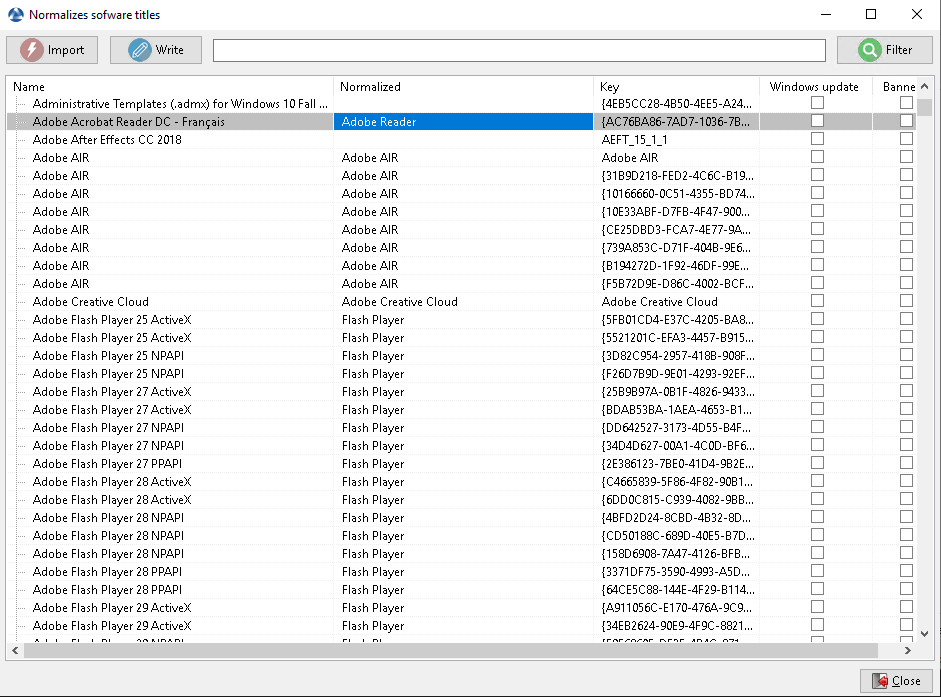
Normalizing the name of software¶
Click Normalize Software Names in the Tools menu.
Select the software to standardize, for example, all different version of Adobe Flash Player.
On the column normalized, press F2 to assign a standardized name to the selected software. Then press Enter.
Note
To select several programs, select them with the shift-up/down key combination.
You can also indicate a software like windows update or banned (Press spacebar in the corresponding column).
Press on Import to load the changes from the server.
Press on Write to save your changes.
You can now run your queries on this standardized name.
Connecting to the WAPT database using a PostgreSQL client¶
You can connect your WAPT database to a client if you prefer to use a PostgreSQL client.
To do so, you’ll have to change some configuration files on your WAPT server.
Find out in which version your PostgreSQL is.
ps -ef | grep -i sql postgres 512 1 0 Jan05 ? 00:00:24 /usr/lib/postgresql/12/bin/postgres -D /var/lib/postgresql/12/main -c config_file=/etc/postgresql/12/main/postgresql.conf
Modify
pg_hba.confof the PostgreSQL version in use. In/etc/postgresql/12/main/pg_hba.conffor Debian and/var/lib/pgsql/12/data/pg_hba.conffor Centos under # IPv4 local connections section, add your address.host wapt all 192.168.0.65/32 md5
where 192.168.0.65 is your IP address that is authorized to connect to the WAPT database.
Allow PostgreSQL to listen on every interface in
/etc/postgresql/12/main/postgresql.conffor Debian and/var/lib/pgsql/12/data/postgresql.conffor Centos, section Connection Settings.listen_addresses = '*'
Restart the service for your PostgreSQL version.
systemctl restart postgresql@12-main.service
Connect to PostgreSQL on waptserver.
sudo -u postgres psql template1
Then give a password to wapt user.
template1=# ALTER USER wapt WITH PASSWORD 'PASSWORD';
Video demonstration¶
Synchronizing WAPT inventories to GLPI  ¶
¶
Working principle¶
WAPT Enterprise offers synchronization between the inventories of your hosts and Glpi ITSM Software.
The method automatically synchronizes changes on your IT infrastructure with the Glpi server.
Installing the required dependencies¶
In order to receive inventories on your Glpi server, you’ll need the FusionInventory plugin on your Glpi server.
Note
After installing FusionInventory, you will have an endpoint on your WAPT server to send the inventories to (…/glpi/plugins/fusioninventory/).
Configuration¶
You can open the window to configure Glpi with .
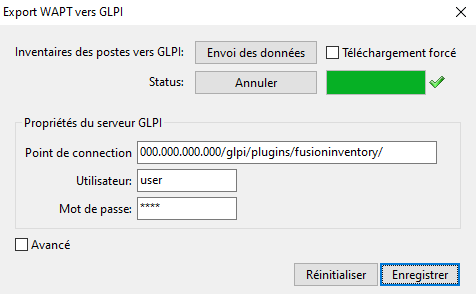
WAPT console showing the Glpi configuration in WAPT¶
In Glpi Server Properties, add the required parameters
in the waptserver.ini configuration file.
[options]
...
glpi_server_endpoint = glpi.mydomain.lan/glpi/plugins/fusioninventory/
glpi_server_user = user
glpi_server_pass = password
glpi_server_pause_timeout = 20,15
glpi_inventory_update_delay = 4
glpi_inventory_update_range = 25
glpi_server_endpoint: url to FusionInventory plugin where to upload inventories on the glpi server;glpi_server_user,glpi_server_pass: Glpi server credentials;glpi_server_pause_timeout= A,B: pause uploading for A seconds when server takes more than B seconds to respond;glpi_inventory_update_range: every how many uploads do you want the database to be updated, if you stop the upload it will restart at last update;glpi_inventory_update_delay= C: The upload is triggered automatically every C hours if not already running;glpi_inventory_debug_directory= example/tmp/glpidirectory to store every XML inventory file that are uploaded to GLPI server (the filename is the machine GUID with.xmlextension. One can use this output to diagnose issue with discrepancies between expected values in GLPI and current values in WAPT.
Using WAPT to send inventory updates to Glpi¶
As you can see on the configuration window you can fill in the settings, trigger or stop an upload right from the WAPT console:
When you fill in Glpi Server Properties, the configuration is registered on the WAPT server when you click Save.
You can retrieve properties already registered on the WAPT server by clicking on Reset (the password is not loaded).
The Endpoint field is the Glpi server url to send the inventories to the
glpi_server_endpoint.You can trigger an upload without waiting for the scheduled task by clicking Upload.
You can stop the upload at any time by clicking Cancel.
Hint
The upload status is updated every 15s, you can follow the progress with the status bar.
If you have many hosts, the upload may take a long time. To avoid this, when the upload is triggered, only inventories that have changed are uploaded:
With
Force uploadevery inventory is uploaded, ignoring already uploaded data.
Advanced use of the Glpi plug-in¶
To display advanced properties, select the Advanced button.
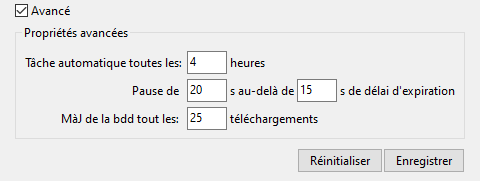
WAPT console showing the Glpi advanced configuration in WAPT¶
The scheduled task runs every Cron every… hours only if the Endpoint is entered. You can disable the scheduled task by leaving the Endpoint empty. ~>
glpi_inventory_update_delay.
Hint
If you want to disable automatic upload, you have to Save an empty Endpoint.
You can trigger pauses (Pause…) when the server response time is too long (over…). ~>
glpi_server_pause_timeout.Update db… sets the database synchronization frequency during upload. ~>
glpi_inventory_update_range.
Adding plugins in the Console¶
To add custom plug-ins, go to Tab.
Creating a custom plug-in for WAPT¶
Click Add to add plug-ins, then edit the corresponding columns.
Column |
Description |
|---|---|
Name |
Name that will appear in the menu. |
Executable |
Path of the executable that will be executed after the click. |
Arguments |
|
Plug-ins will then appear in the menu:
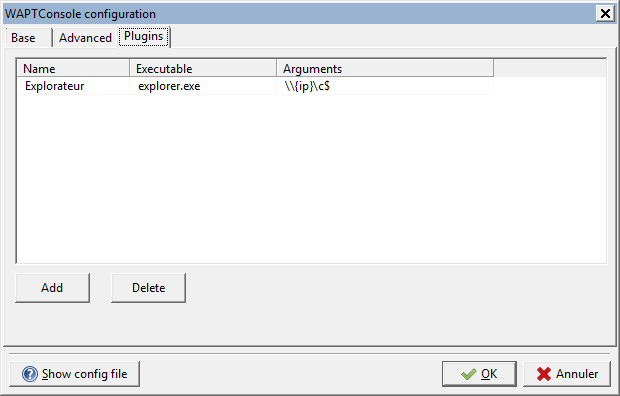
Insert “Explorer” as a plug-n with IP variables¶
Current state of the WAPT to GLPI gateway¶
Inventory items that are currently uploaded to GLPI by the WAPT-GLPI gateway:
Computer name / user name / description / OS name / OS version / language;
CPU / memory / battery / chassis type / physical or virtual;
Network card configuration;
Printer list and properties;
Installed software (not including system wide Appx install);
Network drives;
- Environment variables. Note: currently both system and system-wide
user environment variables are included.
Inventory items that are not currently uploaded to GLPI by the WAPT-GLPI gateway:
Display screens references;
Mouse and keyboard references;
Controllers card references (except graphic card);
Antivirus version;
Firewall state;
Local group list;
Memory bank list and state;
USB ports list and connected devices;
Printer status;
Card readers;
System wide Appx list.
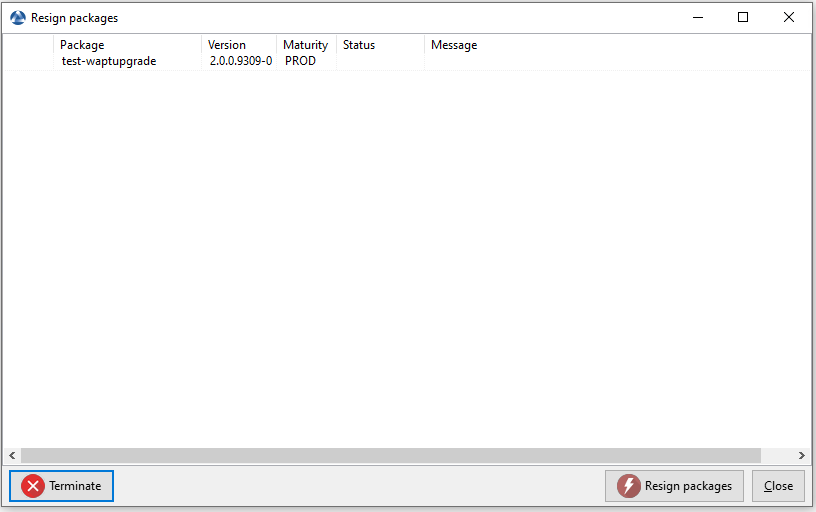
Re-signing all host packages from the WAPT console¶
This method for re-signing all host packages is useful when the underlying cryptographic method or library changes, as this is the case when upgrading from WAPT 1.8.2 (Python 2.7 based) and WAPT >= 2.0 (Python 3.x).
Hint
Use the Administrator’s certificate for re-signing packages.
Host packages¶
Select all host.
Right-click on the selected hosts.
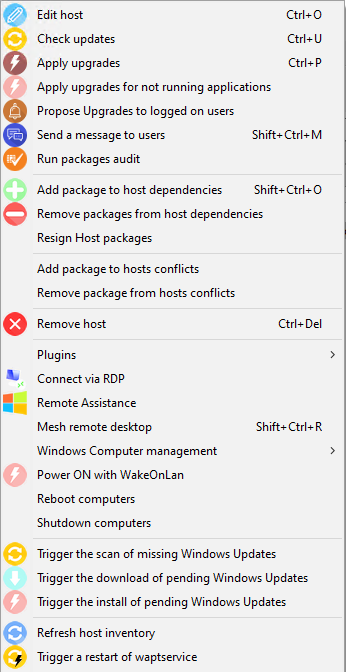
Right-click menu¶
Select Resign Host packages.
Confirm re-signing the selected hosts.
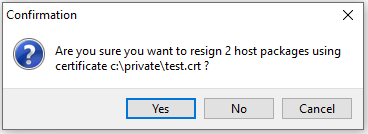
Confirm re-signing selected hosts¶
Then, enter you private key password.
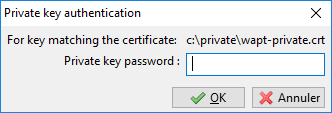
Enter the password for unlocking the private key¶
Selected WAPT host packages are now all re-signed using the new cryptographic method required with Python3.
Other WAPT package types¶
Open the repositories in your WAPT console.
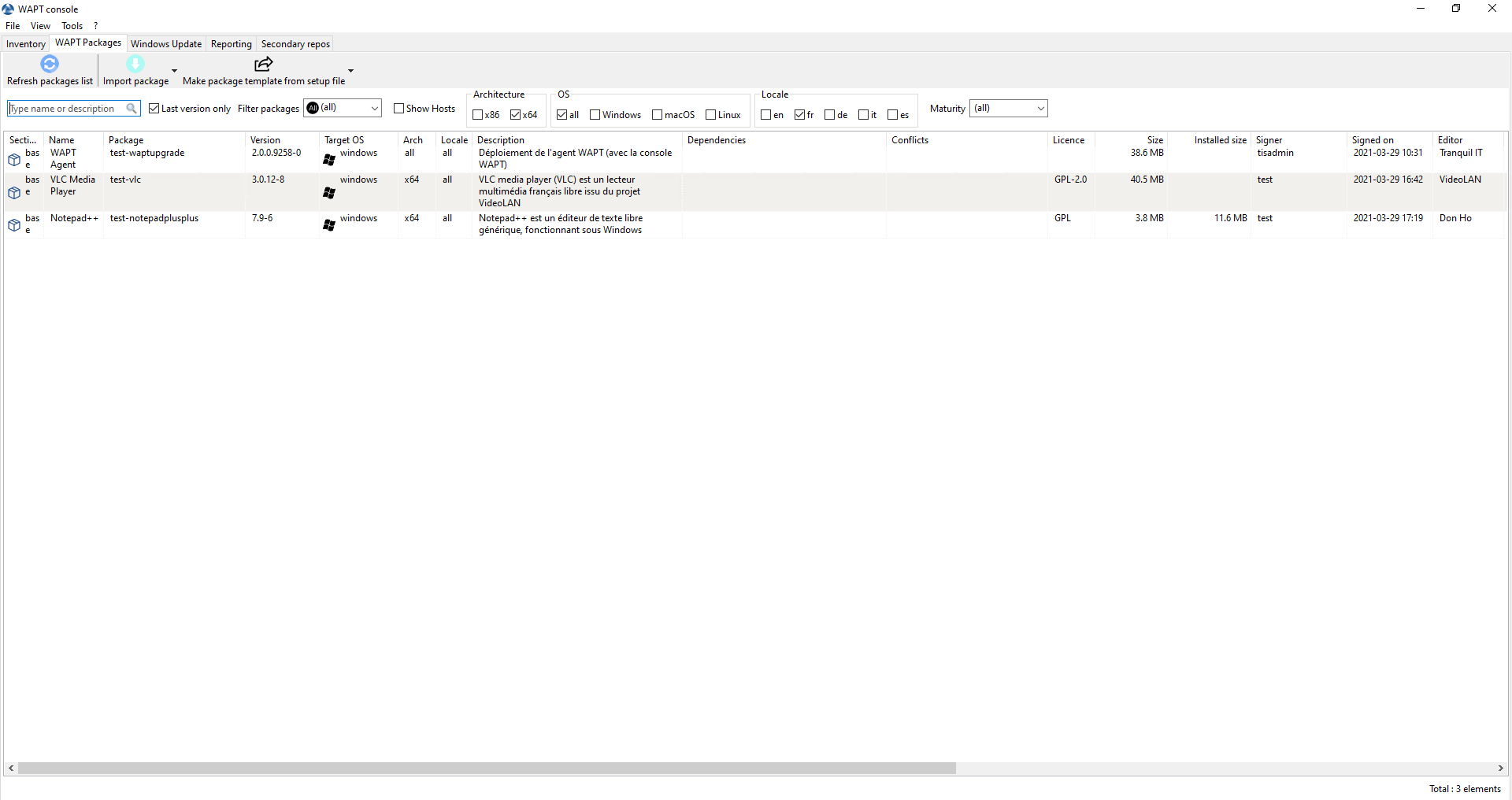
Repositories available on the WAPT console¶
Select all packages in the repository, then right-click on the selection.
Right-click menu¶