5. Configuring the WAPT Agent with advanced options¶
The configuration file wapt-get.ini defines the behavior of the WAPT Agent.
System |
Location |
|---|---|
Windows |
|
Linux |
|
macOS |
|
The [global] section is required.
[global]
After standard installation, the default configuration is:
[global]
waptupdate_task_period=120
wapt_server=https://srvwapt.mydomain.lan
repo_url=https://srvwapt.mydomain.lan/wapt/
use_hostpackages=1
Many parameters other than the above standards can be applied to your agents.
It is possible to make changes in wapt-get.ini by deploying a WAPT config package ( tab “WAPT Packages” → Make package template frome setup file → Host agent dynamic configuration).
In this config package you can put new configuration settings (wua rules, use_repo_rules, etc.).
Note
It is possible to make changes in wapt-get.ini manually, but this will be not persistant if you use a config packages on this host.
An example of package for activate the WAPT Peercache below:
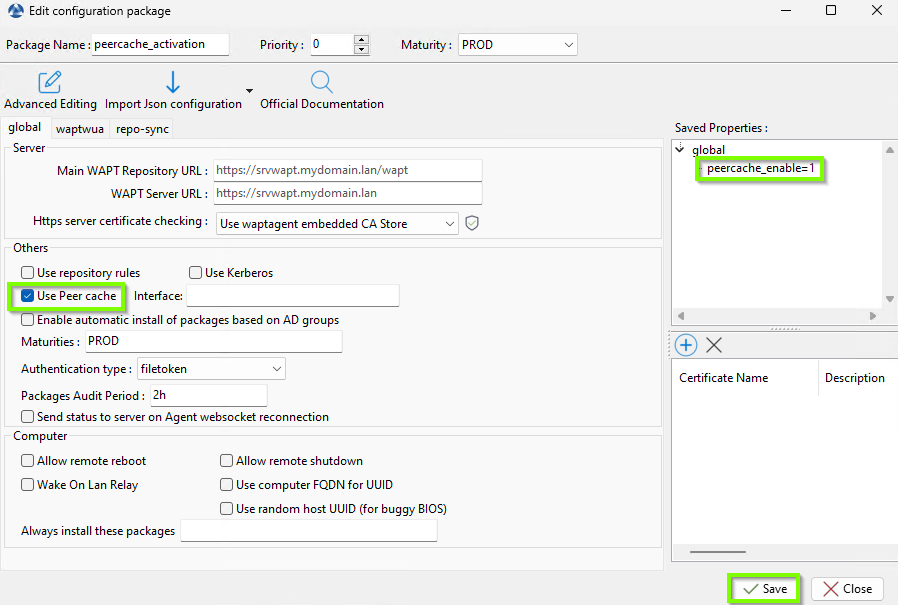
Configuration package to enable peercache¶
5.1. Description of available sections¶
Section |
Description |
|---|---|
|
Global WAPT Agent options. |
|
Main repository options. |
|
External remote repository options. |
|
Repository for host packages options. |
|
WUA Agent options. |
|
For synching multiple repositories. |
All sections are detailed below.
5.2. Description of available options by section¶
5.2.1. [global]¶
5.2.1.1. General settings¶
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Allows to reboot the selected host(s) remotely from the WAPT Console. |
allow_remote_reboot = True |
|
Allows to shut down the selected host(s) remotely from the WAPT Console. |
allow_remote_reboot = True |
|
Forces the package certificate’s date and CRL to be verified. |
check_certificates_validity = True |
|
Path to the local database file. |
dbpath = C:\Program Files (x86)\private\db\waptdb.sqlite |
|
Defines whether a download of pending packages should be started after an update with |
download_after_update_with_waptupdate_task_period = False |
|
Allows to force an Organizational Unit on the WAPT Agent (whether it is in Workgoup or in a domain).
Make sure it respects a consistent case (do not mix “dc”s and “DC”s, for example), which you can find in the Console (in the DN/ |
host_organizational_unit_dn = OU=TOTO,OU=TEST,DC=MYDOMAIN,DC=LAN |
|
Allows to define a WAPT package list that the WAPT Agent MUST install. |
host_profiles = tis-firefox,tis-java |
|
Forces the default language for the GUI (not for package filtering) |
language = en |
|
Allows to set the list of WAPT Agent languages to pre-filter the list of packages visible by the WAPT Agent (for package filtering).
The parameter accepts multiple entries ordered by preference (eg. |
locales = en |
|
Sends the WAPT logs in the Window event log. |
log_to_windows_events = True |
|
Log level of the WAPT Agent. Possible values are: |
loglevel = critical |
|
List of package maturities than can be viewed and installed by WAPT Agent. Default value is |
maturities = PROD, PREPROD |
|
Enables peercache feature |
peercache_enable = True |
|
Address of the main WAPT repository. |
repo_url = https://srvwapt.mydomain.lan/wapt |
|
List of enabled repositories, separated by a comma. Each value defines a section of the |
repositories = repo1, repo2 |
|
Allows the WAPT Console to send anonymous statistics to Tranquil IT. Set to False to disable telemetry. |
send_usage_report = True |
|
Sets how the self service authentication works. Possible values are: |
service_auth_type = filetoken |
|
Defines whether or not it is possible for the user to uninstall applications via the self-service. |
uninstall_allowed = False |
|
For using group packages. Supports nested groups (set ad_groups_use_nested_group = False in wapt-get.ini to disable) |
use_ad_groups = True |
|
Allows to use the FQDN rather than the BIOS UUID as the unique host identifier in WAPT. |
use_fqdn_as_uuid = True |
|
Defines whether host packages are to be used.
|
use_hostpackages = True |
|
Defines whether repositories are replicated. |
use_repo_rules = True |
|
Defines the frequency at which audits are triggered (in minutes). |
waptaudit_task_period = 60 |
|
Defines the WAPT Server URL. If the attribute is not present, no WAPT Server will be contacted. |
wapt_server = https://srvwapt.mydomain.lan |
|
WAPT Agent loopback port. The port is not accessible from the network. |
waptservice_port = 8080 |
|
Defines the update frequency. |
waptupdate_task_period = 24h |
|
Defines the upgrade frequency. |
waptupgrade_task_period = 360 |
|
Enable the WAPT Agent to be used as a Wake-On-Lan relay. |
wol_relay = True |
Note
If there is no
repo_urlattribute in the[global]section, then a repository in the[wapt]section will have to be explicitly defined. It will have to be enabled by adding it to therepositoriesattribute.If there is no
wapt_serverattribute in the[global]section, then no WAPT Server will be used.
5.2.1.2. Settings for the WAPT Server¶
These options will set the WAPT Agent behavior when connecting to the WAPT Server.
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Folder of certificates authorized to verify the signature of WAPT packages. |
|
|
Use kerberos authentication for initial registration on the WAPT Server. |
use_kerberos = True |
|
See the documentation on activating the verification of HTTPS certificates. |
verify_cert = True |
|
WAPT Server URL. If the attribute is not present, no WAPT Server will be contacted. |
wapt_server = https://srvwapt.mydomain.lan |
|
WAPT Server HTTPS connection timeout in seconds. |
wapt_server_timeout = 10 |
5.2.1.3. Settings for the WAPT Exit utility¶
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Prevents users from canceling package upgrades on computer shutdown. If disabled, users will not be able to cancel an upgrade on computer shutdown. |
allow_cancel_upgrade = True |
|
Disables Hiberboot on Windows 10 to make waptexit work correctly. |
hiberboot_enabled = True |
|
Timeout for GPO execution at computer shutdown. |
max_gpo_script_wait = 180 |
|
Timeout for scripts at computer shutdown. |
pre_shutdown_timeout = 180 |
|
Prevents the software upgrade if the software is currently running on the host (impacted_process attribute of the package). |
upgrade_only_if_not_process_running = True |
|
Only upgrade packages with a specific priority. |
upgrade_priorities = high |
|
Delay (in seconds) before the automatic start of the installations. |
waptexit_countdown = 25 |
|
Allows or prevents packages to be upgraded during waptexit |
waptexit_disable_upgrade = False |
5.2.1.4. Settings for the WAPT Self-Service and the WAPT service Authentification¶
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Useful with |
ldap_auth_base_dn = dc=mydomain,dc=lan |
|
Useful with |
ldap_auth_server = srvads.mydomain.lan |
|
Defines the authentication system of the WAPT service, available value are |
service_auth_type = filetoken |
|
Apply selfservice package view filtering for Local Administrators. |
waptservice_admin_filter = True |
|
sha256 hashed password when waptservice_user is used (the value NOPASSWORD disables the requirement for a password). |
waptservice_password = 5e884898da |
|
Forces a user to authenticate on the WAPT service. |
waptservice_user = admin |
5.2.1.5. Settings for the the WAPT System Tray utility¶
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Prevents the WAPT System Tray utility from sending notifications (popup). |
notify_user = True |
5.2.1.6. Settings for the Proxy¶
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Defines the address of the HTTP proxy. |
http_proxy = http://user:pwd@host_fqdn:port |
|
Use a proxy to access the repositories. |
use_http_proxy_for_repo = True |
|
Use a proxy to access the WAPT Server. |
use_http_proxy_for_server = True |
5.2.1.7. Settings for creating WAPT packages¶
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Defines the default prefix for new or imported packages. Prefix is case sensitive, we recommand to use lower case. |
default_package_prefix = doc |
|
Defines the directory for storing packages while in development. |
default_sources_root = C:\waptdev |
|
Defines the path to the Administrator’s private key. |
personal_certificate_path = c:\Users\wapt-adm\Desktop\wapt-adm.crt |
5.2.2. [waptwua] 
 ¶
¶
Refer to configuring WAPTWUA on the WAPT Agent.
5.2.3. [wapt]¶
If this section does not exist, parameters are read from the [global] section.
5.2.4. [wapt-templates]¶
External remote repositories that will be used in the WAPT Console for importing new or updated packages. The Tranquil IT repository is set by default.
5.2.5. [wapt-host]¶
Repository for host packages. If this section does not exist, default locations will be used on the main repository.
More information on that usage can be found in this article on working with multiple public or private repositories.
5.2.6. [repo-sync] 
 ¶
¶
Configuration for remote repositories, this section must exist ONLY if the WAPT Agent is a remote repository.
More information on that usage can be found in this article on configuring multiple repositories.
5.3. Settings for using multiple repositories¶
To add more repositories, new [repository_name] sections can be added in wapt-get.ini.
Active repositories are listed in the repositories attribute of the [global] section.
This parameter can be configured both in the WAPT Agent configuration and in the WAPT Console configuration file C:\Users\%username%\AppData\Local\waptconsole\waptconsole.ini.
For information on configuring the WAPT Console, please refer to this documentation.