4. Configuring WAPT repositories¶
4.1. Repository location on the WAPT Server¶
Operating System |
Value |
|---|---|
Debian and derivatives |
|
RedHat and derivatives |
|
Windows |
|
4.2. Replicating a repository 
 ¶
¶
4.2.1. Functional overview¶
Hint
The method explained below is for the Enterprise version only.
The deprecated and unsupported Syncthing method may be used for the Discovery version of WAPT.
4.2.1.1. WAPT Agent replication role¶
Repository replication can be enabled using a WAPT Agent installed on an existing host, a dedicated appliance or a Virtual Host.
The replication role is deployed through a WAPT package that enables the Nginx web server and configures scheduling, packages types, packages sync, and much more.
This feature allows WAPT Agents to find dynamically their closest available WAPT repository from a list of rules stored on the WAPT Server.
4.2.1.2. Replication behavior¶
Repository replication in WAPT is handled by WAPT Agents natively.
It is based on a sync.json file which indexes every files present in these folders:
wapt;waptwua;wapt-host;wads.
Enabling replication has the following effects:
Once
enable_remote_repois enabled on a WAPT Agent, it will sync packages locally inside thelocal_repo_pathfolder.It adds the WAPT Agent in the Repositories tab as a Remote repository, enabling new actions such as Force Sync or Check files.
By default, only the wapt folder is synchronized, you can select which folder to sync by adding up elements in
remote_repo_dirsparameters.Synchronization period can be configured with
local_repo_time_for_sync_startandlocal_repo_time_for_sync_stopparameters.Bandwidth allocated to sync can be configured with
local_repo_limit_bandwidth.
Every parameters of WAPT repository sync MUST be set in the [repo-sync] section of the WAPT Agent wapt-get.ini configuration file.
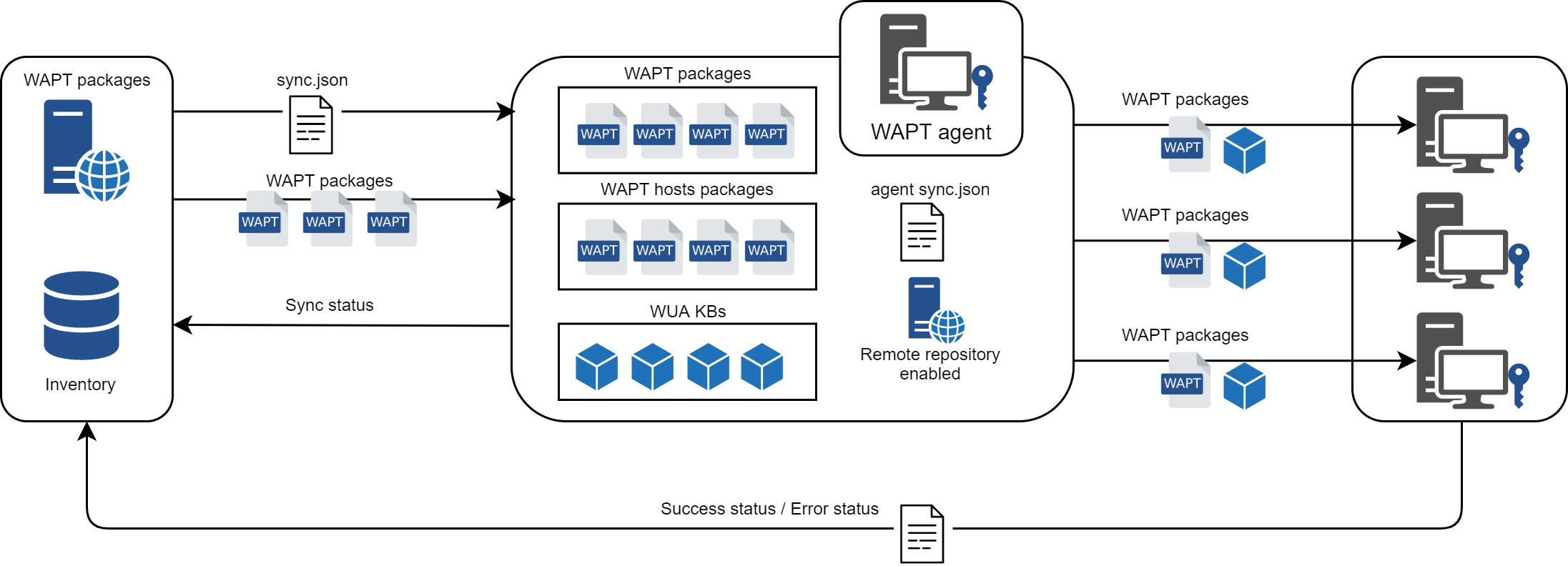
Flow diagram of the replication behavior of the WAPT Agent¶
4.2.2. WAPT Agent configuration¶
Several packages are available in Tranquil IT public store to enable repository replication on Windows or Linux based WAPT Agents.
An initial conf package exists on our repository WAPT packages configuration (tis-remote-repo-conf), You can modify the package to customise the configuration of your secondary repositories.
For Windows repository use this ready-to-use WAPT packages for Windows (tis-remote-repo-http).
For Linux repository use this ready-to-use WAPT packages for Linux (tis-remote-repo-nginx).
This way, the desktop of the welcome desk in a remote office of any organization may become a WAPT repository to distribute WAPT packages to the fleet of computers in the remote office.
This special package:
Installs and enables the Nginx web server on the remote repository.
Configures Nginx virtualhost environment.
Enables remote repository configuration in
wapt-get.ini.
It is possible to automatically configure repositories with your own preferred values by editing this package.
To enable replication on an existing WAPT Agent (Linux / Windows), you need to set in the [repo-sync] section in the wapt-get.ini configuration file of the WAPT Agent.
Hint
If you use DNS, please remind to create a DNS entry for your WAPT agent.
Options (Default Value) |
Definition |
Example |
|---|---|---|
|
Enables remote repository to synchronize with the main repository. |
|
|
Sets the path to the root directory of the local repository for WAPT packages. |
|
|
Sets synchronization start time (HH:MM / 24h format). |
|
|
Sets synchronization stop time (HH:MM / 24h format). |
|
|
Sets synchronization periodicity (minutes). |
|
|
Sets synchronization allowed bandwidth (MBytes/s). |
|
|
Defines folders to synchronize. |
|
|
Enables for use repository rules. |
|
|
Synchronizes the repository only if forced. |
|
Warning
If you modify manually wapt-get.ini on the remote repository, you need to restart the WAPT service.
Note
Below is an example wapt-get.ini file for a WAPT Agent.
[global]
...
use_repo_rules = True
[repo-sync]
enable_remote_repo = True
local_repo_path = D:\WAPT\
local_repo_time_for_sync_start = 20:30
local_repo_time_for_sync_end = 05:30
local_repo_sync_task_period = 25
local_repo_limit_bandwidth = 4
remote_repo_dirs = wapt,waptwua,wads
4.2.3. WAPT Server configuration¶
By default, the WAPT Server will know which WAPT Agents are configured as remote repositories and it will list them in the WAPT Console.
4.2.4. Repository rules¶
When a WAPT Agent has been configured as a repository, it will automatically retrieve its rules.json file from the WAPT Server.
The rules.json file is a signed .json file that contains a list of sorted rules to apply to the remote WAPT Agents, so they may connect to their most appropriate repositories.
If no rules can be matched, the WAPT Agent will fallback to the repo_url attribute defined in its wapt-get.ini configuration file.
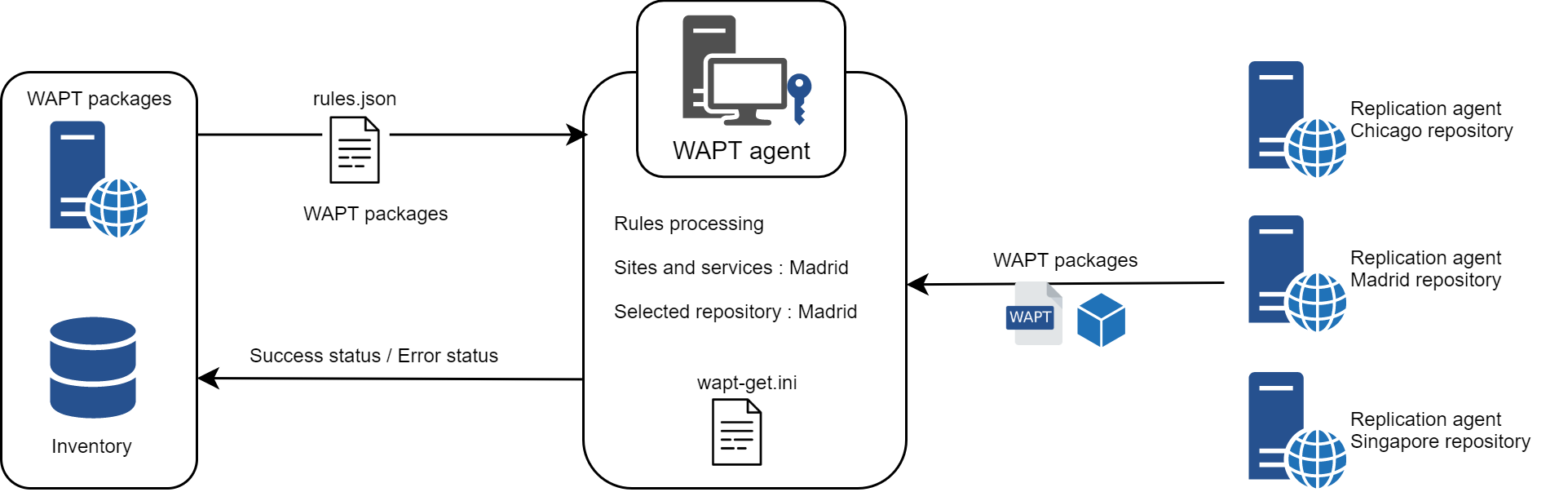
4.2.4.1. WAPT Agent¶
Warning
If you have configured GeoIP redirects on Nginx, you should disable it as it might conflict with repository rules.
To enable WAPT Agent repository rules, you MUST enable this setting in the [global] section of the wapt-get.ini configuration file of the WAPT Agent.
Options (Default Value) |
Description |
Example |
|---|---|---|
|
For using replicating repository. |
|
Below is an example wapt-get.ini file for a WAPT Agent.
[global]
...
use_repo_rules = True
Note
It is possible to enable this option when generating a WAPT Agent.
4.2.4.2. WAPT Server¶
On the WAPT Server, remote repositories functionality is automatically enabled.
To verify, edit waptserver.ini and read remote_repo_support value.
Options (Default Value) |
Example value |
Definition |
|---|---|---|
|
|
Enables the WAPT Server to serve as a repository. |
4.2.4.3. WAPT Console¶
Repository rules can be managed from the WAPT Console and are based on several parameters:
Options |
Example value |
Description |
|---|---|---|
Agent IP |
|
Defines a repository rule based on Agent IP sub-network. |
Domain |
|
Defines a repository rule based on Active Directory domain name. |
Hostname |
|
Defines a repository rule based on the hostname of the WAPT Agent. |
Public IP |
|
Defines a repository rule based on the public IP address (NATed hosts). |
Site |
|
Defines a repository rule based on Active Directory Sites and Services. |
4.2.4.3.1. Adding a repository rule¶
To add a new repository rule, go to the Repositories tab in the WAPT Console and click on the Add rule button.
Options |
Example value |
Description |
|---|---|---|
Name |
repo25 |
Defines the name for the repository rule. |
Condition |
AGENT IP |
Defines the condition to match for the repository rule to apply (see above). |
Value |
192.168.25.0/24 |
Defines the value when the condition applies. If NOT is checked, the value applies to the reverse of the condition. |
Repository URL |
Defines the list of available remote repositories. The list includes http://download.windowsupdate.com/microsoftupdate/v6/wsusscan/ to allow directly downloading of Windows Updates by the remote repositories to preserve WAPT Server bandwidth. If your certificate is self-signed, continue to use HTTP. |
|
Package type |
WAPT |
Defines what types of packages are replicated. |
Other |
No fallbacks |
The option No Fallback will prevent from falling back to the main WAPT Server and will avoid undesired network congestion if the remote repository becomes temporarily unavailable. |
The option Proxy will need to be set if the remote repository is required to connect via a proxy.
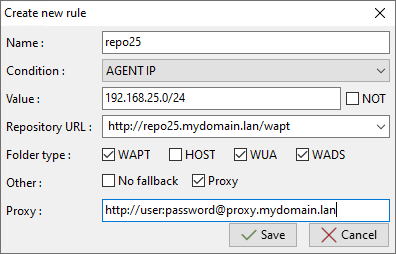
Window for setting repository rules in the WAPT Console¶
You can then choose from the different above parameters and affect values to a specific secondary WAPT repository.
Warning
The rules are applied from top to bottom.
The first rule that matches the conditions overrides all the other rules placed under.
Danger
Do not forget to save the replication rules.
4.2.5. Delete a repository¶
For clean removal, we recommend the following actions:
Remove the rules linked to the repository to be decommissioned. On the WAPT Console by right-click on the rule and delete rule.
Uninstall the packages remote-repo-conf and http or nginx, on the repository agent.
If necessary, clean up the directory containing the WAPT packages. Default location for Windows
C:\wapt\waptserver\repository, for Debian and derivatives/var/www/wapt/, for RedHat and derivatives/var/www/html/wapt/
4.3. Multiple repositories¶
Similar to Debian repositories, it is possible for the WAPT Agent to use multiple repositories for updating package. The WAPT Agents will check all repositories.
Danger
If you use this functionality, KNOW WHAT YOU ARE DOING.
When using repositories with different signers, the additional signer’s public certificates MUST be added to C:\Program Files (x86)\wapt\ssl on Windows or /opt/wapt/ssl on Linux and macOS, therefore, you MUST trust their work and their signature.
You then MUST deploy the WAPT Agents with both keys.
Please refer to the documentation on creating the WAPT Agent to add certificates.
4.3.1. WAPT Agent configuration¶
This parameters are modifiable on wapt-get.ini file.
4.3.1.1. Description of available parameters¶
Options |
Example value |
Description |
|---|---|---|
|
repositories = wapt-templates,private |
Defines the repositories, for example |
|
[wapt-templates] repo_url=https://store.wapt.fr/wapt verify_cert = True [private] repo_url=https://srvwapt.mydomain.lan/wapt verify_cert = False |
Defines the properties of each repository declared in the |
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Defines the HTTP proxy address. |
http_proxy = http://user:pwd@host_fqdn:port |
|
Defines the address of the main WAPT repository. |
repo_url = https://srvwapt.mydomain.lan/wapt |
|
Defines the timeout when connecting to remote repositories (in miliseconds). |
timeout = 5000 |
|
Defines whether a proxy needs to be set to access the repositories. |
use_http_proxy_for_repo = True |
|
Defines whether HTTPS certificates of the repository needs to be verified, and if so defines the path to the certificate bundle. However if you certificate is self-signed, continue to use http. |
verify_cert = True |
Note
The WAPT Agent will look for updates in all repositories defined in its wapt-get.ini configuration file when doing a wapt-get search.
More info on using WAPT with the command line interface.
4.3.2. Configuring the WAPT Console for using multiple repositories¶
After having configured the WAPT Agent for using multiple repositories, we can make the repositories show up in the WAPT Console.
To do so, modify the %appdata%\local\waptconsole\waptconsole.ini file.
Example:
[wapt-template]
repo_url = https://wapt.tranquil.it/wapt
http_proxy =
verify_cert = True
public_certs_dir =
client_certificate =
client_private_key =
timeout = 5
[private]
repo_url = https://srvwapt.mydomain.lan/wapt
http_proxy =
verify_cert = False
public_certs_dir =
client_certificate =
client_private_key =
timeout = 5
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Defines the folder that contains the certificates used to authenticate downloaded external packages. |
client_certificate = |
|
Defines the folder that contains the private key. |
client_private_key = C:\Program Files (x86)\wapt\ssl\server\srvwapt.mydomain.lan.pem (on Windows) |
|
Defines the HTTP proxy address. |
http_proxy = http://user:pwd@srvproxy.mydomain.lan:port |
|
Defines the folder that contains the certificates used to authenticate downloaded external packages. |
public_certs_dir = C:\private |
|
Defines the address of the main WAPT repository. |
repo_url = https://srvwapt.mydomain.lan/wapt |
|
Defines the timeout when connecting to remote repositories (in miliseconds). |
timeout = 5000 |
|
Defines whether HTTPS certificates of the repository needs to be verified, and if so defines the path to the certificate bundle. However if you certificate is self-signed, continue to use HTTP. |
verify_cert = True |